1. Don’t underestimate the importance of the system security plan
A robust system security plan (SSP) is a critical foundation. While generic templates are helpful in building a comprehensive SSP, they only cover the 110 controls — and not all 320 objectives that are required by CMMC 2.0.
Tailor your SSP to address all the objectives of CMMC 2.0. You must go beyond the templates for compliance.
2. Don’t underestimate CMMC’s cost and complexity
As mentioned above, for a company to move from an “average” level of cybersecurity readiness to being “assessment ready” for CMMC, it typically takes about 12 to 18 months. This time frame underscores the extent of preparation and changes required, which can include updating systems and policies, as well as training employees.
Below is a chart from the Department of Defense estimating the cost of an assessment when the new rule is in place. Note that it does not take into account the time, effort and cost of becoming compliant, nor any technical controls that you may also need to purchase.
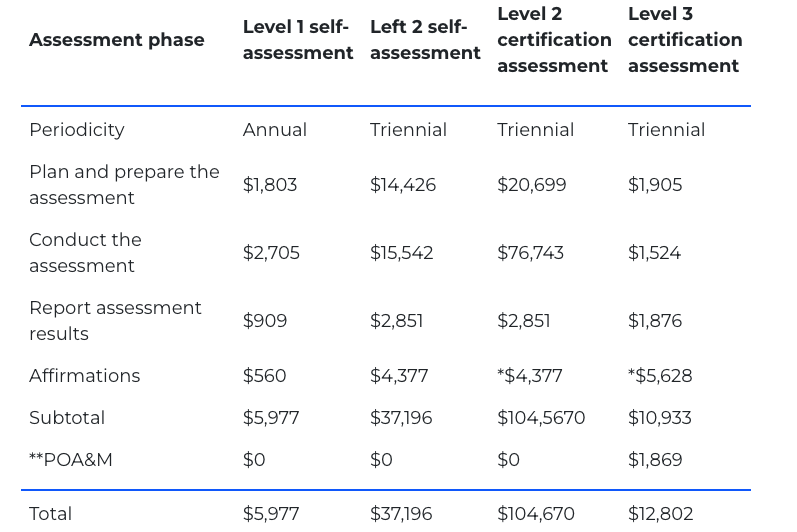
*Reflects the three-year cost to match the periodicity.
**Requirements “NOT MET” (if needed and when allowed) will be documented in a Plan of Action and Milestones.
3. Don’t overlook CMMC 2.0 controls in policies and procedures
Thoroughly documenting, following and auditing policies and procedures is essential for meeting control objectives. Compliance starts with documentation, and it should also be regularly reviewed, tested and improved upon.
Organizations often err by not maintaining a detailed, organized documentation system, as nearly every control requires a corresponding written policy. One policy can cover multiple controls and objectives; just make sure your policies clearly state rules and commitments to meet specific controls.
Also, ensure that your procedures are clear and that practices, like auditing and maintenance, are well structured. Even the smallest companies should have a process for auditing and reviewing practices.
4. Don’t ignore employee training and awareness
The whole organization must live within a security culture. And technical controls alone are not sufficient. Annual employee security and awareness training are critical to creating a safe and compliant environment.
Educate your staff on procedures for common security threats like phishing and train them to handle sensitive information like your FCI and CUI. Require role-based training and issue regular updates to keep everyone informed. Lapses in training can increase vulnerabilities.
5. Don’t overlook risk management
Third-party due diligence and risk assessments, which involve evaluating vendors and partners as well as analyzing risks, are critical and often missed components. Regular risk assessments, due diligence and strategic decisions about those assessments are an important part of information protection. Neglecting this aspect can expose you to significant risks.
How Wipfli can help
We understand the intricacies of CMMC compliance and offer tailored solutions to navigate its complexities, along with all our robust and agile cybersecurity services. To learn more, see our cybersecurity services page.

.jpg?h=404&iar=0&w=539&rev=80dcd3deec9a4fa79e5148c94597b723&hash=B93A7D98B02196256C47ED09783C8B0D)